The breach of VMProtect: 2 major incidents
VMProtect leak
In 2023, VMProtect, a commercial virtualization-based protector for executable files, was leaked — not once, but twice.
First, a dump of the protector popped up in May 2023:
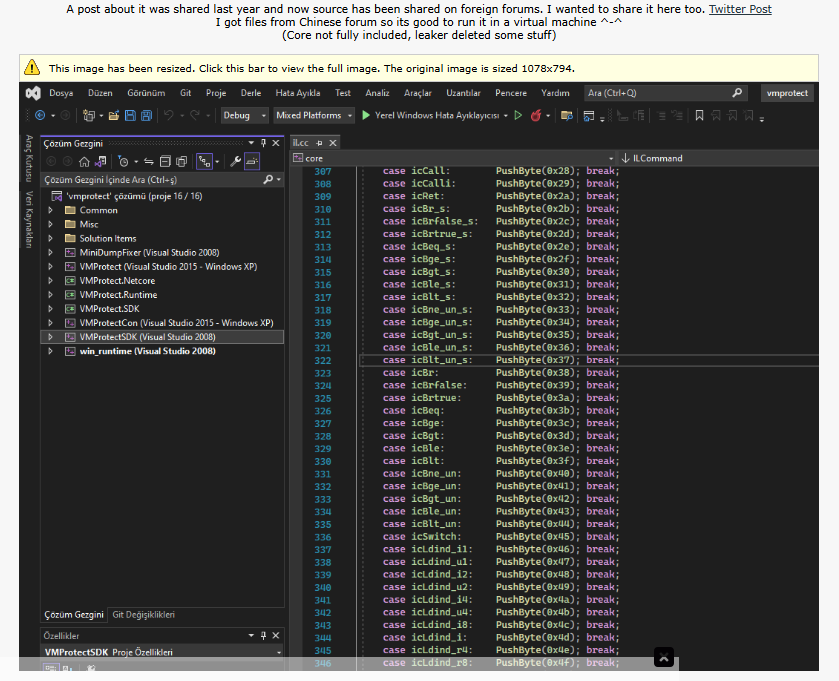
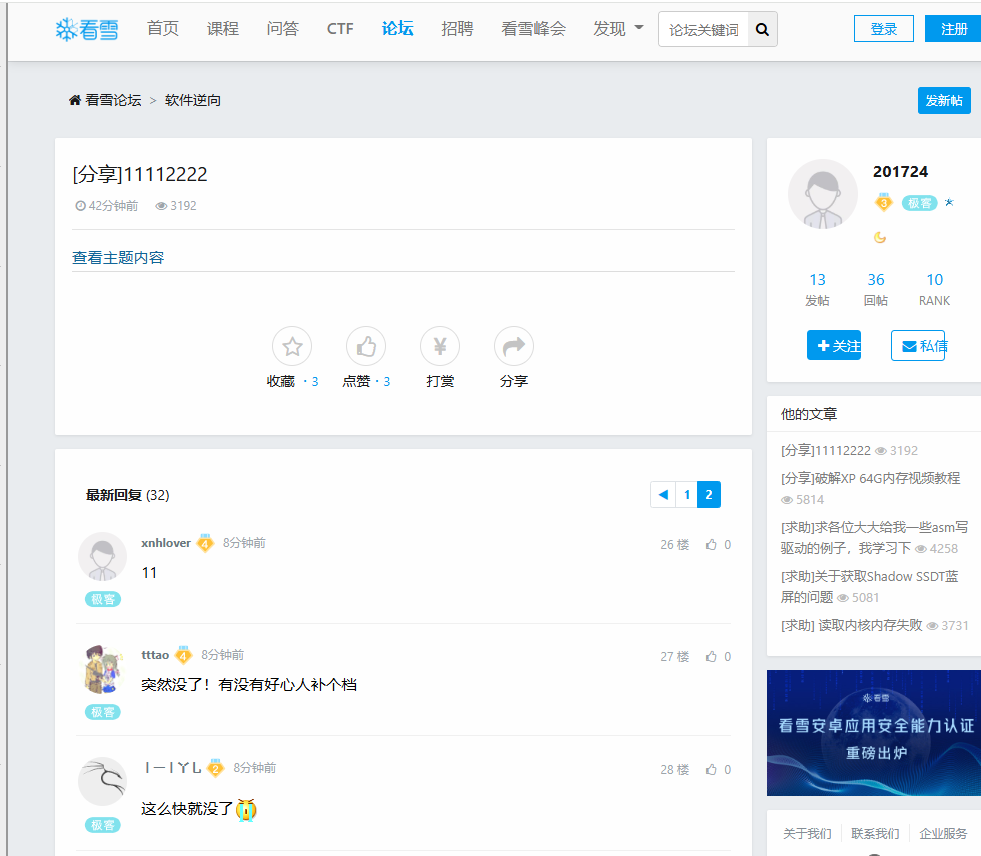
This dump was shared via the Chinese Kanxue Security Forum, frequently used for sharing software cracks:
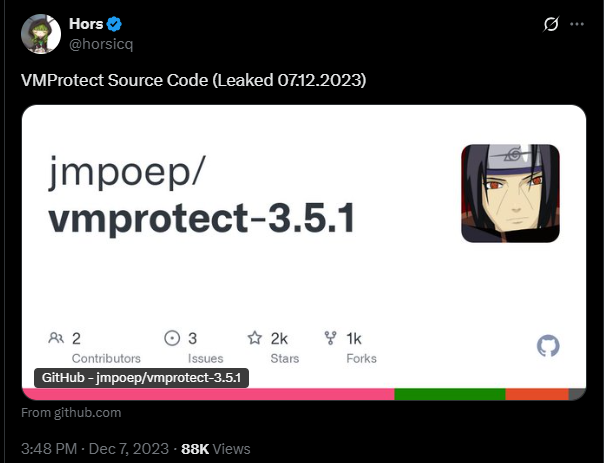
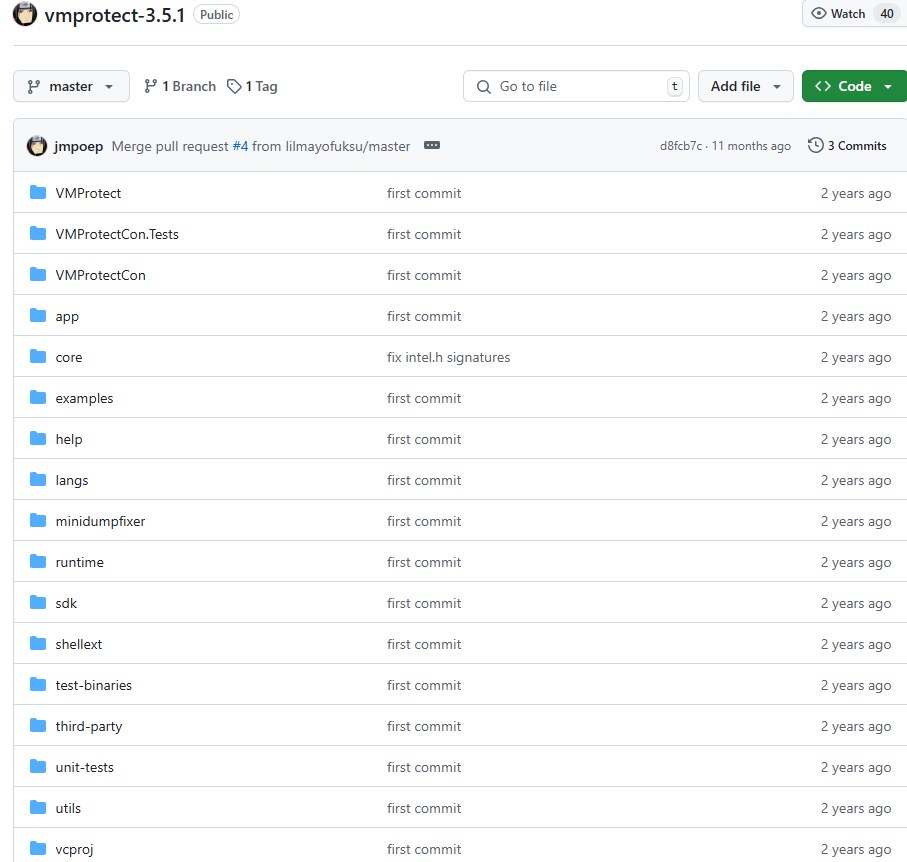
Then, about half a year later, the more complete archive was leaked (7 Dec 2023) and posted on GitHub:
Timeline
-
May 2023 : Large chunk of VMProtect 3.x codebase leaked, first public confirmation that the code was in the wild.[1][2][3][4]
-
December 2023 : A second, packaged dump advertised as the “full” source was released on Github. Still missing a few files such as the ARM back-end, demanglers, but enough to compile parts of the tool.[1]
There was no evidence of an internal hack at VMPSoft, the consensus is an outsider stole the code (likely from a customer portal or reseller) and leaked it.
Is VMProtect “cracked” now?
Yes and no; having the source code made it possible to partially compile VMProtect:
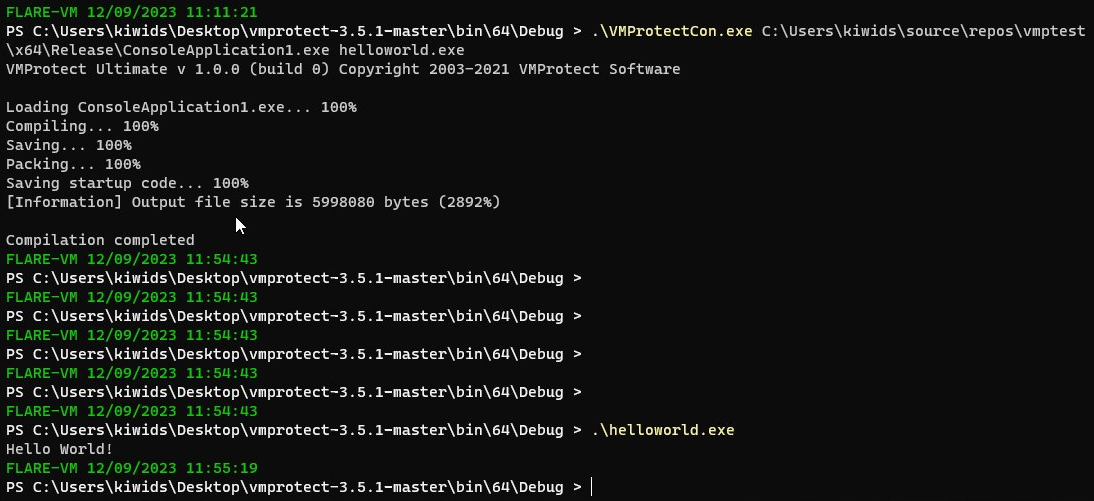
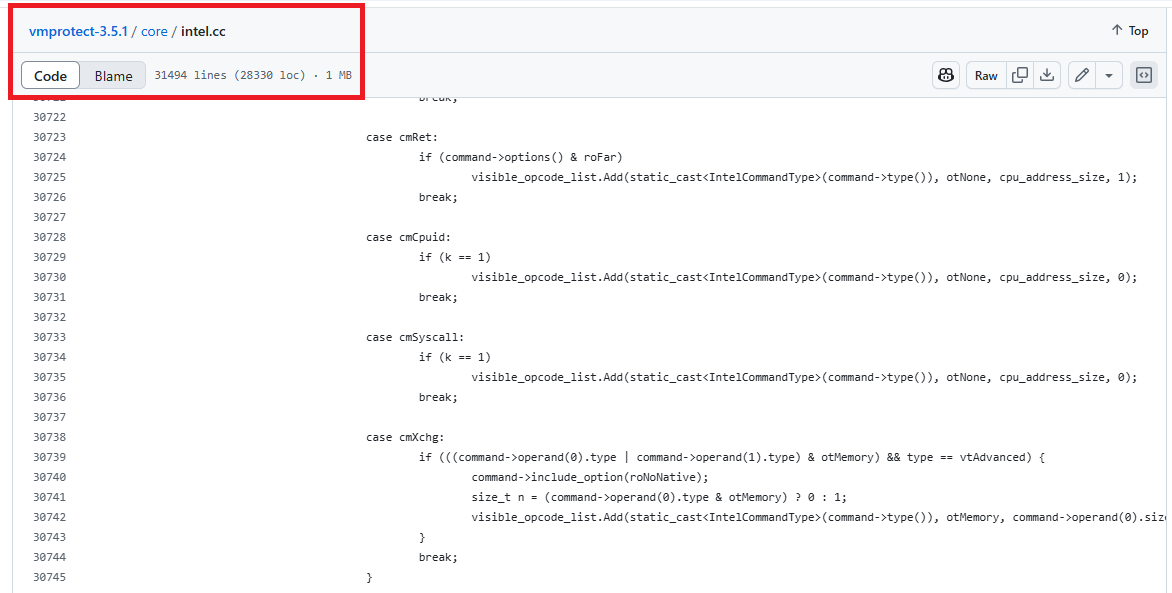
The core virtualization module (intel.cc) was of main interest to reverse engineers / crackers; in total, it amounted to roughly 31000 lines of raw C++!
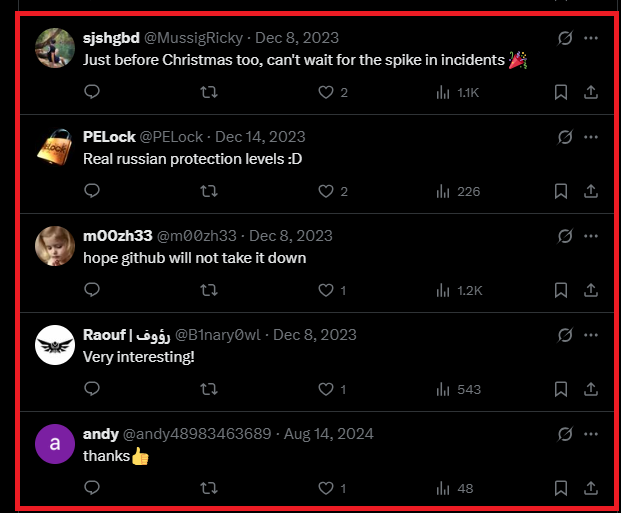
The community’s response
Overall, the reverse engineering community welcomed the breach of VMProtect, with some even describing it as a “Christmas gift” 🎁:
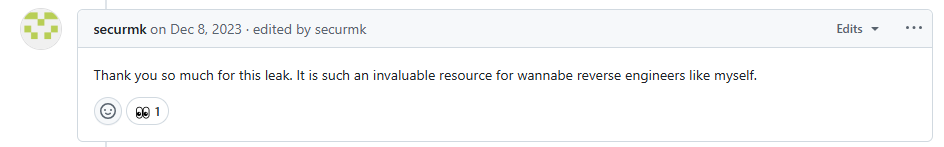
securemk thought the breach was an “invaluable resource” for wannabe reverse engineers like him:
Moving forward
Personally, I see this as a temporary blow to VMProtect’s reputation in the software protection community. Still, they’ve probably prepared for these kinds of situations, and as of 2025, the protector is still kicking:
I hope you found this post interesting!

Leave a comment